Routing Traffic Through TorGuard in OPNsense
Dec 1, 2024 • opnsense
Routing IPv4 traffic through TorGuard, complete with an integrated killswitch and the option to exclude selected devices.

This post took way longer than expected to write. What started as my first post created has now become my fifth one published. There are plenty of tutorials, even official ones, explaining how to configure VPNs, with kill switches and other features I didn't even understand and blindly followed along. After days of troubleshooting, I couldn't get it to work properly, so I tried to configure it in my own way. In this post, I want to show you, how I successfully set up a connection to a VPN, in this case, TorGuard. (not sponsored)
Prerequisites
- You have an up and running OPNsense instance on version 24.7
- You have an active TorGuard subscription, or an existing WireGuard configuration
Preparation (TorGuard)
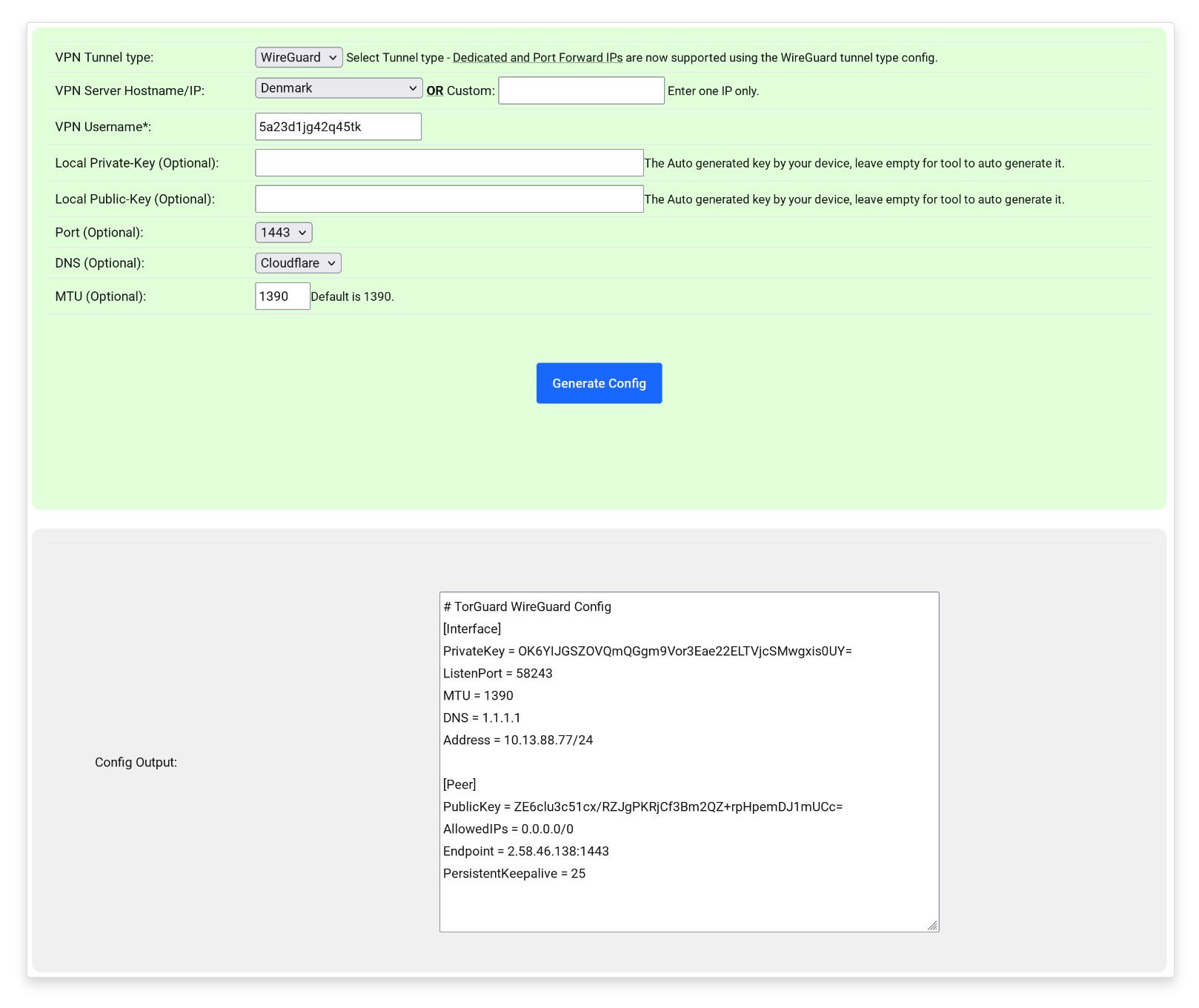
Before you do anything in OPNsense, you'll need to generate a WireGuard config file. If you already have one, you can go ahead and skip this section. Otherwise, go to the TorGuard config page, then select the following parameters:
| Key | Value |
|---|---|
| VPN Tunnel type | WireGuard |
| VPN Server Hostname/IP | whatever you want |
| VPN Username | your TorGuard username |
| Local Private-Key | empty |
| Local Public-Key | empty |
| Port | 1443 |
| DNS | Cloudflare |
| MTU | 1390 |
Click on Generate Config. The config file will be downloaded automatically and displayed on the site too. In my case it looks like this here:
# TorGuard WireGuard Config
[Interface]
PrivateKey = OK6YIJGSZOVQmQGgm9Vor3Eae22ELTVjcSMwgxis0UY=
ListenPort = 58243
MTU = 1390
DNS = 1.1.1.1
Address = 10.13.88.77/24
[Peer]
PublicKey = ZE6clu3c51cx/RZJgPKRjCf3Bm2QZ+rpHpemDJ1mUCc=
AllowedIPs = 0.0.0.0/0
Endpoint = 2.58.46.138:1443
PersistentKeepalive = 25
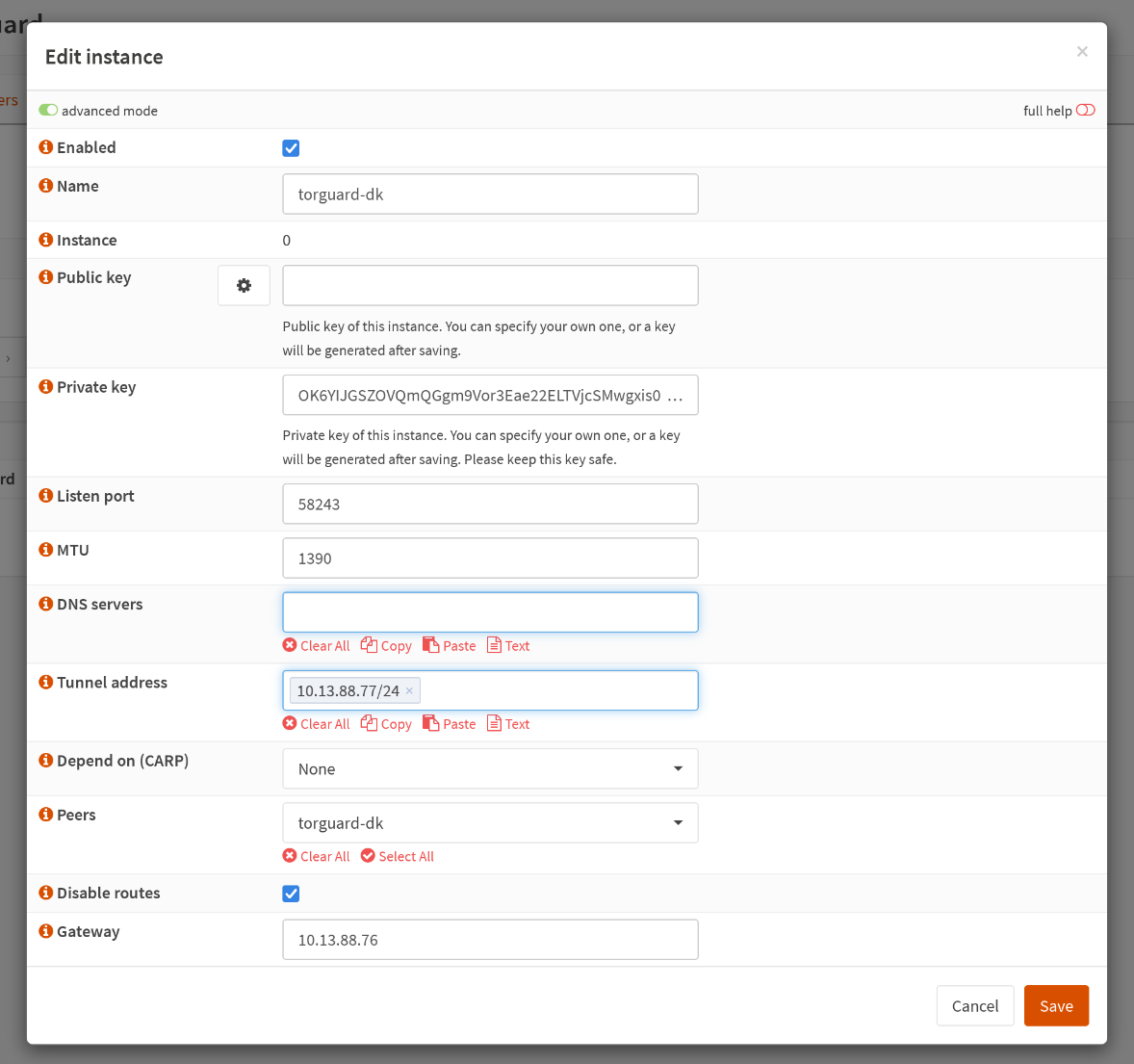
Configuring OPNsense
Open the OPNsense web UI, then use the sidebar to go to:
VPN > WireGuard > Instances
Click on the small + button, in the bottom right corner, to add a new WireGuard instance. In the form, enable advanced mode. It's the small toggle in the top left corner and fill out the form:
| Key | Value |
|---|---|
| Name | anything you want, mine is torguard-dk |
| Public key | empty |
| Private key | config value: [Interface] > PrivateKey |
| Listen port | config value: [Interface] > ListenPort |
| MTU | config value: [Interface] > MTU |
| DNS servers | empty |
| Tunnel address | config value: [Interface] > Address |
| Depend on (CARP) | None |
| Peers | empty (for now) |
| Disable routes | checked |
| Gateway | [Interface] > Address - 1 (e.g. 10.13.88.77 -> 10.13.88.76) |
Save it.
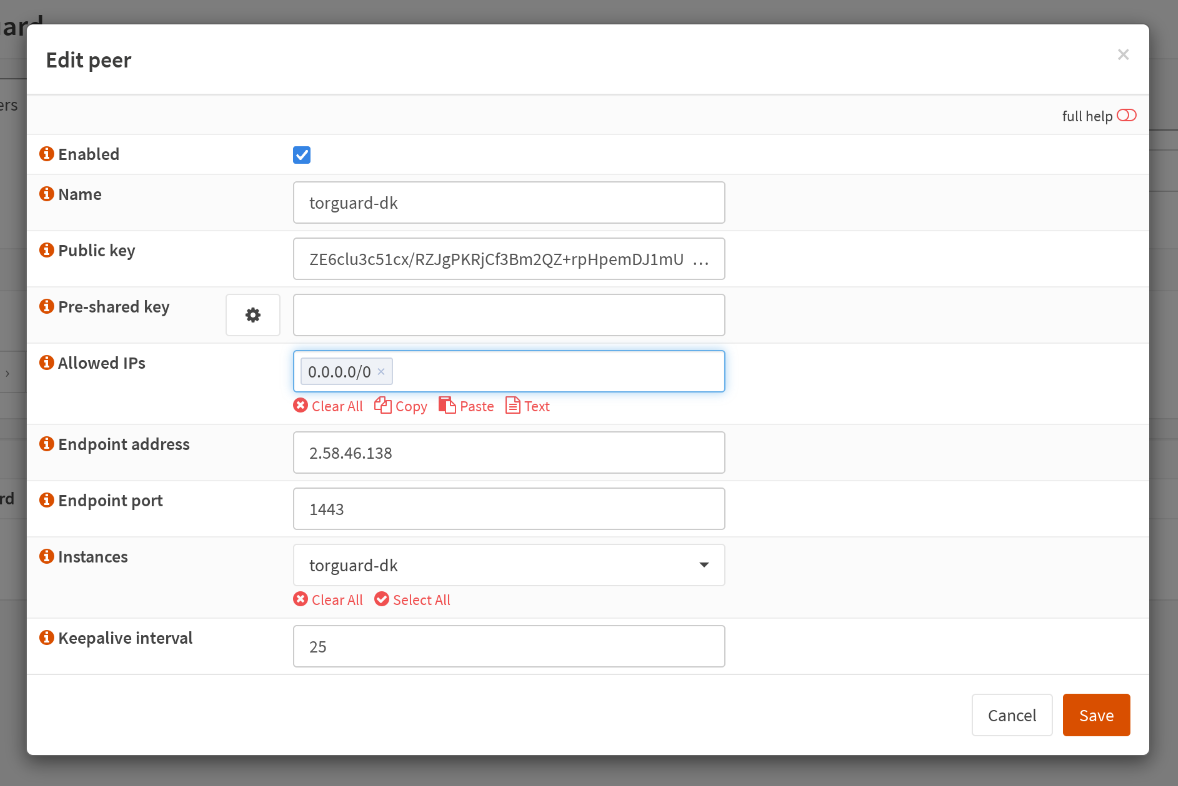
VPN > WireGuard > Peers
Do the the same here as before. Click on the + button, to add a new WireGuard peer, and fill out the form:
| Key | Value |
|---|---|
| Enabled | checked |
| Name | anything you want, mine is torguard-dk |
| Public key | config value: [Peer] > PublicKey |
| Pre-shared key | empty |
| Allowed IPs | 0.0.0.0/0 |
| Endpoint address | config value: [Peer] > Endpoint |
| Instances | select your previously created instance, mine is torguard-dk |
| Keepalive interval | 25 |
Save it. Under the table, check the box for Enable Wireguard and click on Apply.
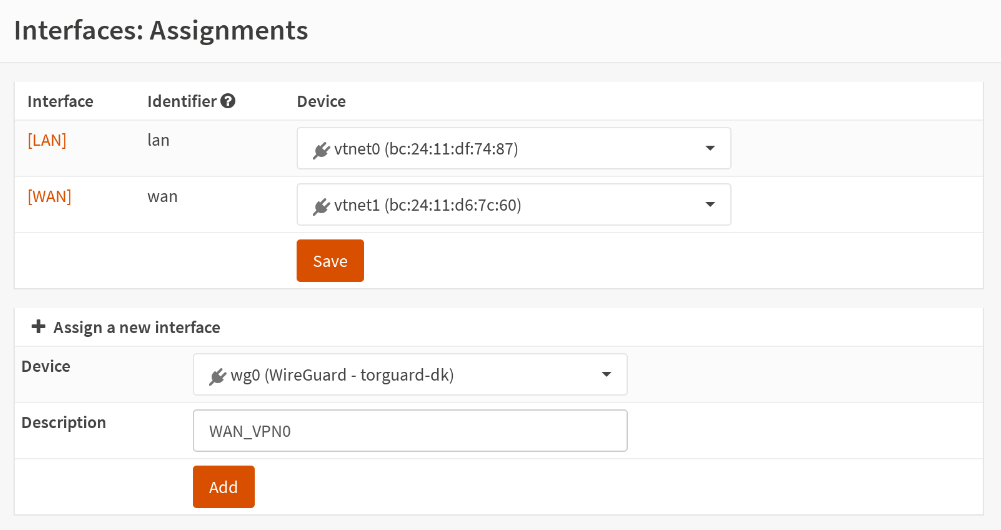
Interfaces > Assignments
In this step you're gonna assign the created WireGuard instance to an interface. In the table that says Assign a new interface do the following:
| Key | Value |
|---|---|
| Device | select the WireGuard instance with the name you chose for it, mine is torguard-dk |
| Description | WAN_VPN0 (feel free to use any other name, it will be the name of your new interface) |
Then click on Add.
Interfaces > [WAN_VPN0]
Simply enable the interface and lock it. Nothing else needs to be done here. Save the changes.
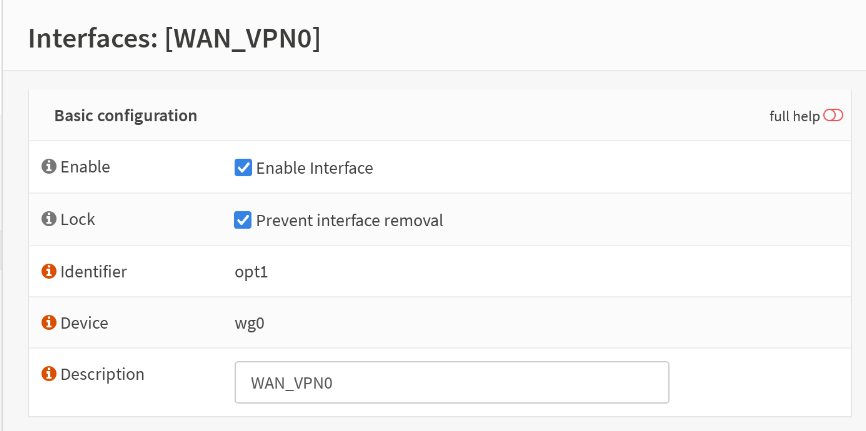
System > Settings > General
Disable gateway switching and save the changes.
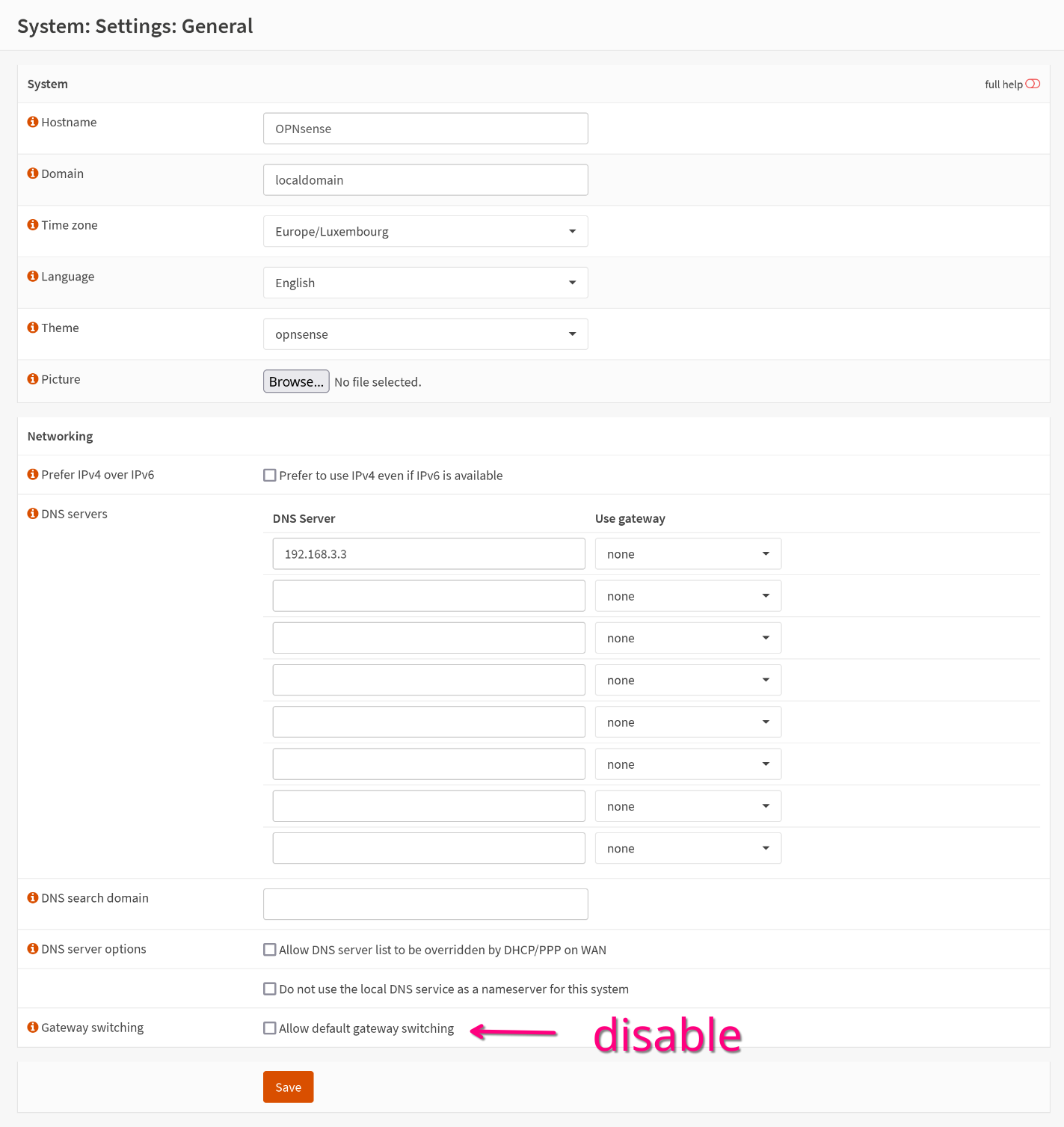
System > Gateways > Configuration
Add a new gateway:
| Key | Value |
|---|---|
| Name | give it a name |
| Interface | WAN_VPN0 |
| IP Address | the IP address that you subtracted 1 from |
| Far Gateway | checked |
| Disable Gateway Monitoring | unchecked |
| Monitor IP | I use the VPNs internal DNS server (10.8.0.1 or 10.9.0.1 for TorGuard) |
Save it and Apply changes.
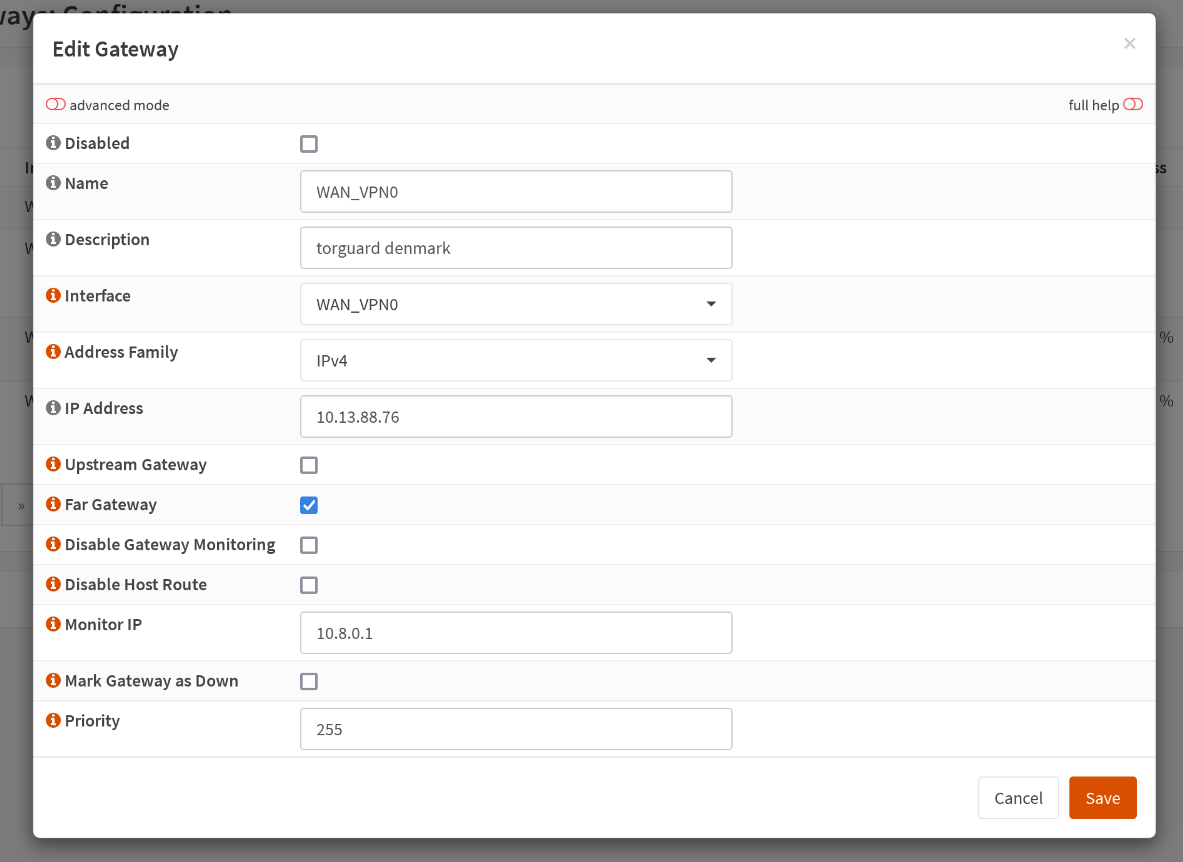
Firewall > NAT > Outbound
Change the mode to Hybrid outbound NAT rule generation, and click on Save.
Now, add a new manual rule and leave everything unchanged, except for the following:
| Key | Value |
|---|---|
| Interface | WAN_VPN0 |
Save and Apply the changes.
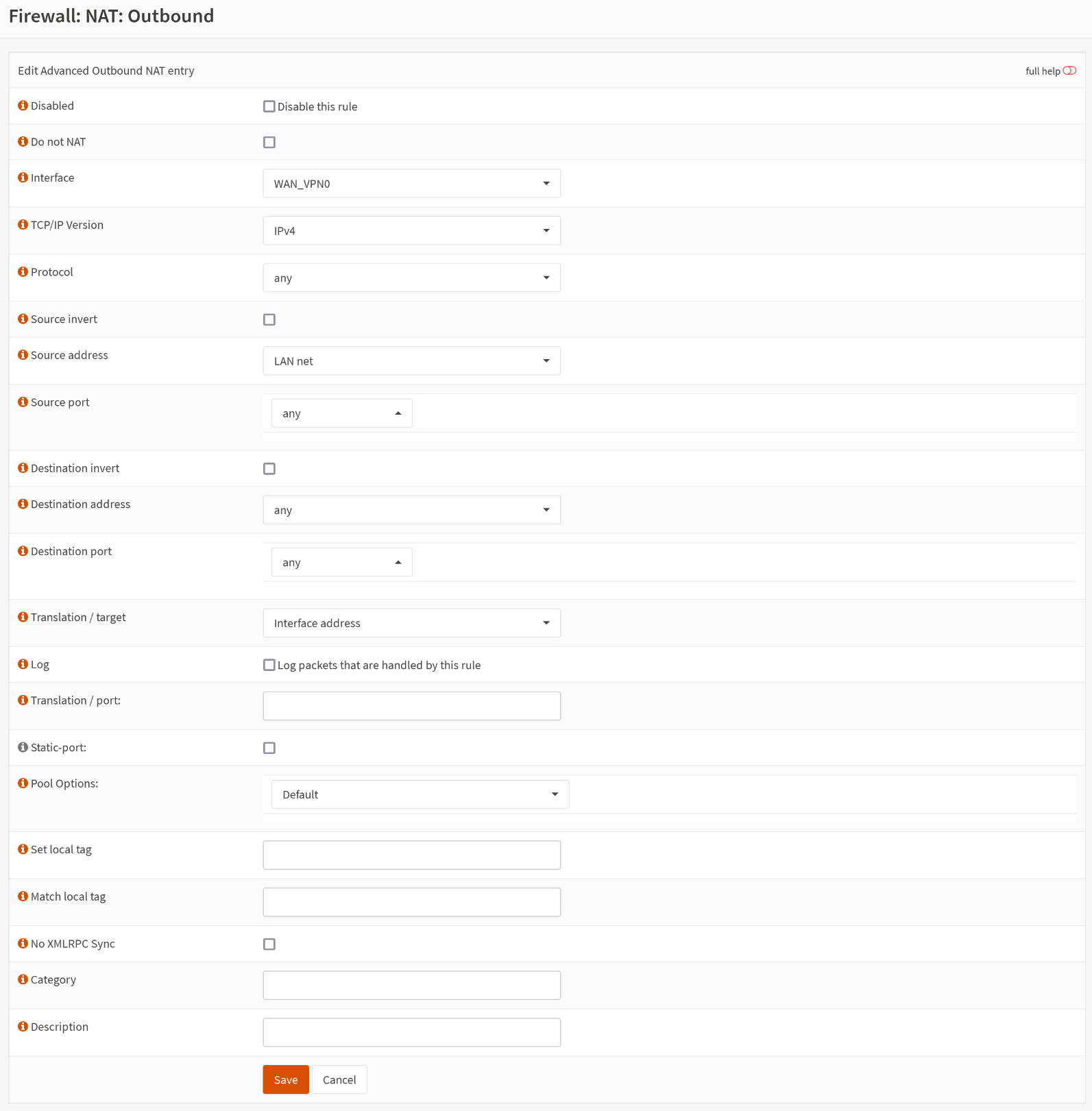
Firewall > Rules > LAN
Create a new rule. Leave everything unchanged unless mentioned here:
| Key | Value |
|---|---|
| Action | Pass |
| Interface | LAN |
| Source | Single host or Network |
| Source | enter the address of your LAN subnet, like 192.168.1.0/24 |
| Gateway | WAN_VPN0 |
LAN net as Source. It won't let WireGuard establish a connection to the VPN after a restart. Same goes for changing the gateway from default to VPN of the default rule.Save it.
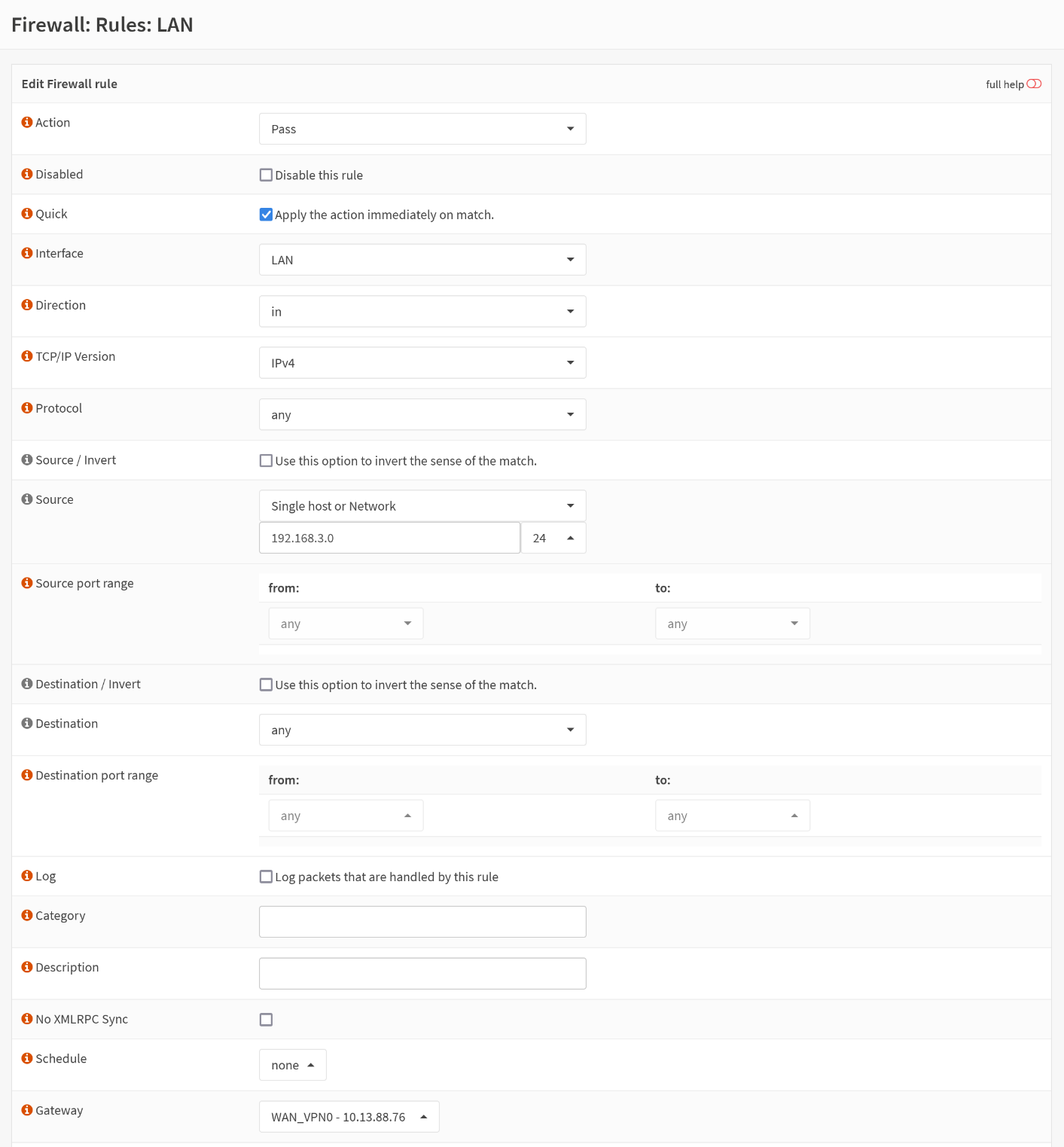
After saving the changes. you'll be redirected to Firewall > Rules > LAN. There, select your created rule (1), and move it above the default rule (2). Then apply the changes (3).
By prioritizing the VPN rule, all the outbound traffic will be routed through it, which acts as a kill switch too. Don't take my word for it though, as any higher prioritized firewall rules can override this behavior.
Selective routing (optional)
In this section, I will show you how you can exclude specific devices from being routed through the VPN gateway. Feel free to skip this step if it's not needed.
Firewall > Aliases
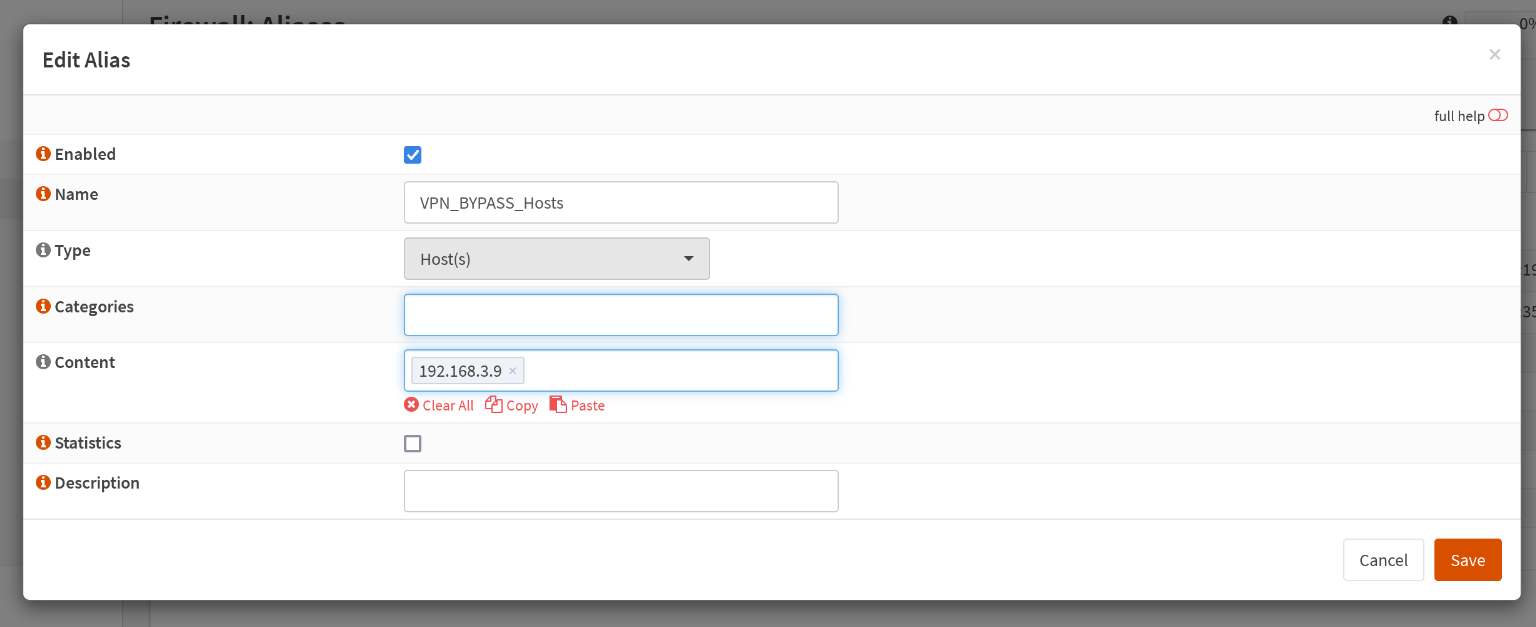
Otherwise, click on the + button to add a new alias. Fill out the form:
| Key | Value |
|---|---|
| Enabled | checked |
| Name | VPN_BYPASS_Hosts |
| Type | Hosts (but it really depends on your use case, you can select whatever you need) |
| Categories | up to you, otherwise empty |
| Content | 192.168.3.9 (again, change the value to your use case. I just let this specific host bypass the VPN) |
| Statistics | up to you, otherwise unchecked |
| Description | up to you, otherwise empty |
Save it, and don't forget to Apply the changes below the table.
Firewall > Rules > LAN
Create a new rule:
| Key | Value |
|---|---|
| Action | Pass |
| Interface | LAN |
| Source | VPN_BYPASS_Hosts |
| Gateway | WAN_GW |
Save it.
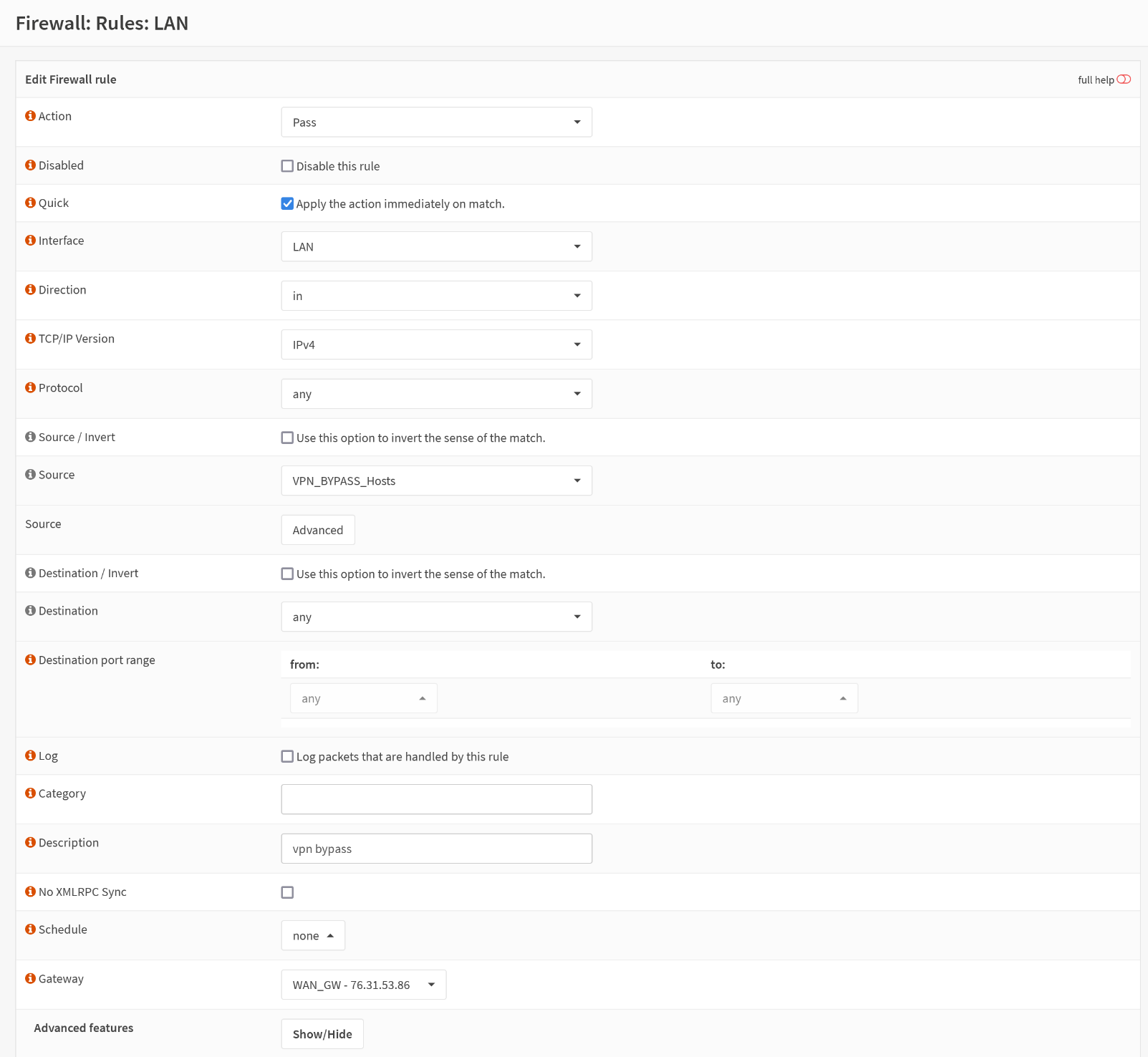
Select the new created rule and move it above the VPN rule. Then Apply changes.
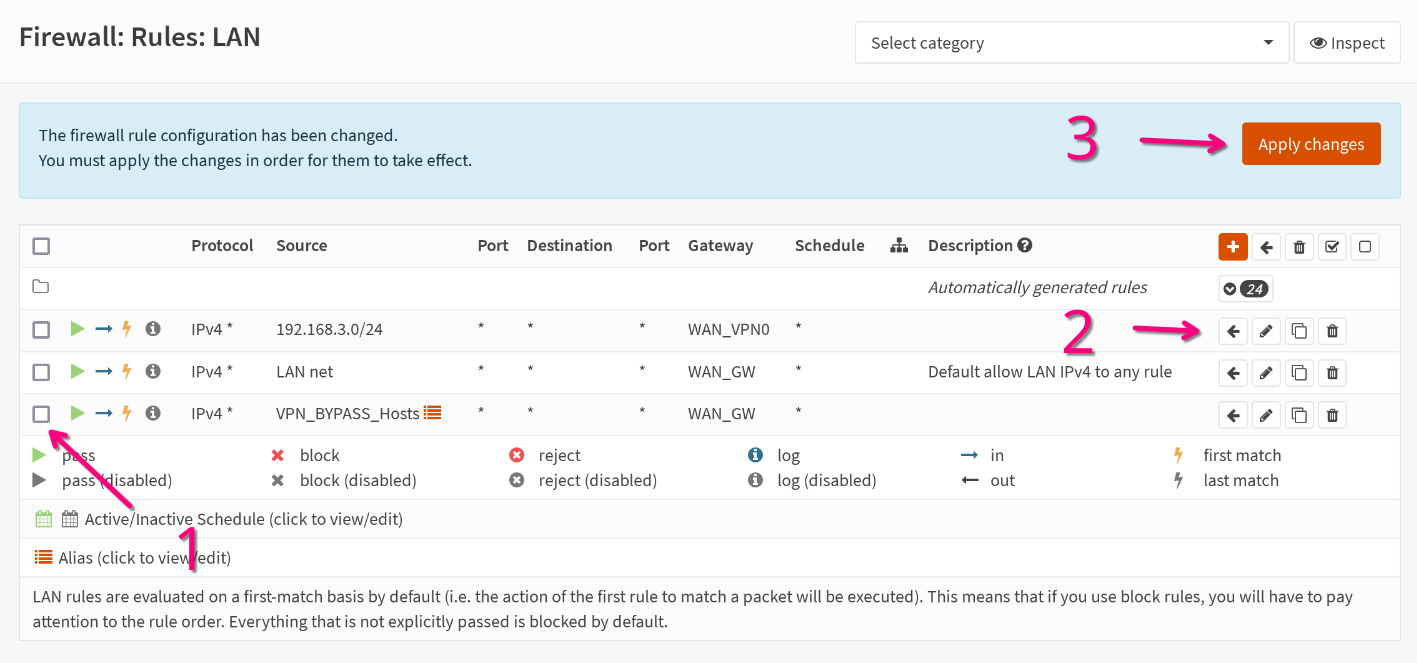
And you are done!